Meow's CyberAttack - Application/Server Attacks - Replay Attacks
book:
- S+ 7th ch9
Meow’s CyberAttack - Application/Server Attacks - Replay Attacks
Replay Attacks
Replay attacks: becoming quite common
a kind of access or modification attack.
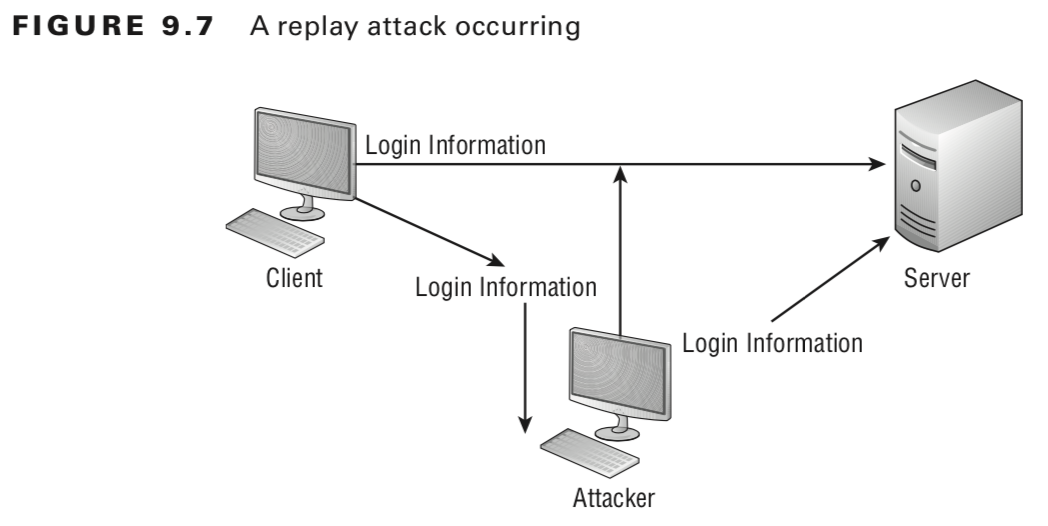
occur when information is captured over a network. The attacker capture the information and replay it later .
also occur with security certificates from systems
the attacker will have all of the rights and privileges from the original certificate.
This is the primary reason that most certificates contain a unique session identifier and a time stamp.
If the certificate has expired, it will be rejected,
and an entry should be made in a security log to notify system administrators.
Example:
This post is licensed under CC BY 4.0 by the author.
Comments powered by Disqus.