Meow's CyberAttack - Application/Server Attacks - Injection - Directory Traversal / Command Injection
book:
- S+ 7th ch9
- CEH Prep ch13
Meow’s CyberAttack - Application/Server Attacks - Injection - Directory Traversal / Command Injection
Directory Traversal / Command Injection
directory traversal attack:
- gain access to restricted directories (like root directory) through HTTP
.
is a specific type of command injection attack
attempts to access a file by including the full directory path, or traversing the directory structure >.
gain access to the root directory of a system (limited by administrative users), essentially gain access to everything on the system.
the root directory of a website is far from the true root directory of the server;
an absolute path to the site’s root directory is something in IIS (Internet Information Services), like
C:\inetpub\wwwroot.If an attacker can get out of this directory and get to
C:\windows, the possibility for inflicting harm is increased exponentially.
command injection attack
simplest ways to perform directory traversal.
injects system commands into computer program variables such that they are executed on the web server.
Example:
exploiting weak IIS implementation by calling up a web page along with parameter cmd.exe?/c+dir+c:\ , call the command shell and execute a directory listing of the root drive (C:\) .
With Unicode support, entries such as %c%1c and %c0%af can be translated into
/and\, respectively.
The ability to perform command injection is rare these days.
Most vulnerability scanners will check for weaknesses with
directory traversal/command injectionand inform you of their presence.To secure, run such a scanner and keep the web server software patched.
Example:
Unix systems, the passwd file includes user logon information, and it is stored in the
/etcdirectory with a full directory path of/etc/passwd- Attackers use commands:
../../etc/passwdor/etc/passwdto read the file.
- Attackers use commands:
a command was entered
the attacker was attempting to gain access to the password file within the
/etcdirectory.If the attacker tried to inject code, they would not use commands, but rather PHP, ASP, or another language.
they could use a remove directory command (such as
rm -rf) to delete a directory, including all files and subdirectories.
prevention
prevent these types of attacks
- Input validation.
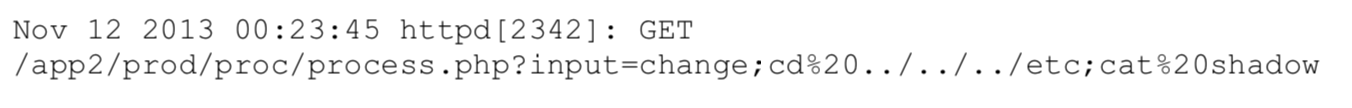
Comments powered by Disqus.