GCP - Cloud IAM
Cloud IAM Identity and Access Management
Overview IAM objects
GCP resource hierarchy
Zones and regions physically organize the GCP resources Projects logically organize the GCP resources
The GCP resource hierarchy
- helps you manage resources across multiple departments and multiple teams within the organization.
- define a hierarchy to create trust boundaries in resource isolation
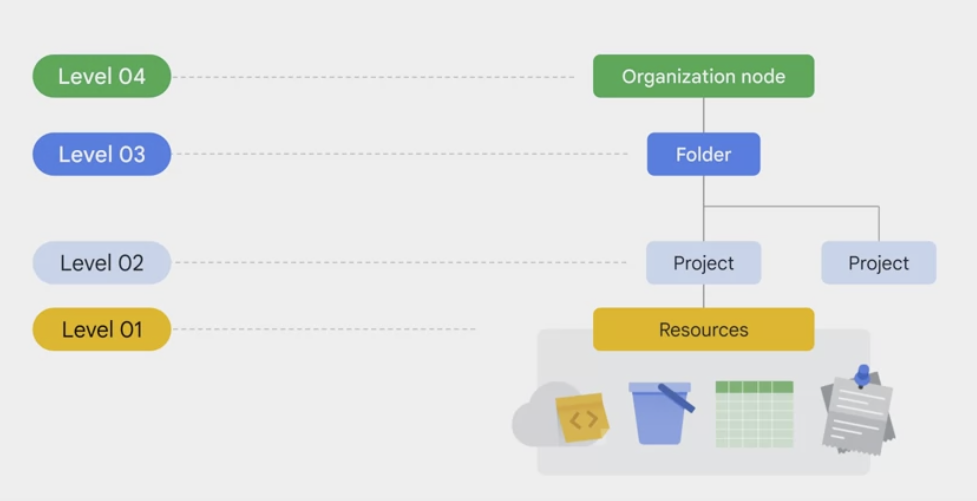
functional structure of Google Cloud consists of four levels: resources, projects, folders, and an organization node.
Resourcesin Google Cloud represent virtual machines, Cloud Storage buckets, tables in BigQuery, or any other component in Google Cloud.Projectsare the second level in the resource hierarchy and are used to enable and manage Google Cloud services, such as APIs, billing, collaborators, and other Google services.Foldersallow for the assignment of policies and permissions to resources at a granular level.- can contain projects or other folders, and resources within a folder inherit policies and permissions from that folder.
- useful for grouping resources based on departments or teams within an organization.
- organization node
- encompasses all projects, folders, and resources.
- Special roles, such as
organization policy administratorandproject creator, can be assigned to theorganization nodeto control access and permissions. - The creation of a new organization node depends on whether the company is a Google Workspace customer or not.
- Folders and projects are considered “children” of the organization node.
Organization
organization owns all the folders beneath it.
the root node of a GCP resource hierarchy.
having organization is required for you to use folders.
G Suite customer already it
- organization admin:
- provide access to administer all resources belonging to his organization
- is useful for auditing.
- project creator:
- allows a user to create projects within organization.
Folder
- Projects can belong to a folder, which is another grouping mechanism.
- use folders to reflect their hierarchy of the enterprise and apply policies at the right levels within the enterprise.
- can nest folders inside of folder
Project
- the base level organizing entity for
- creating and using resources and services, and managing billing APIs, and permissions.
The GCP resources must belong to a project.
Projects can be easily created, managed, deleted, or even recovered from accidental deletions.
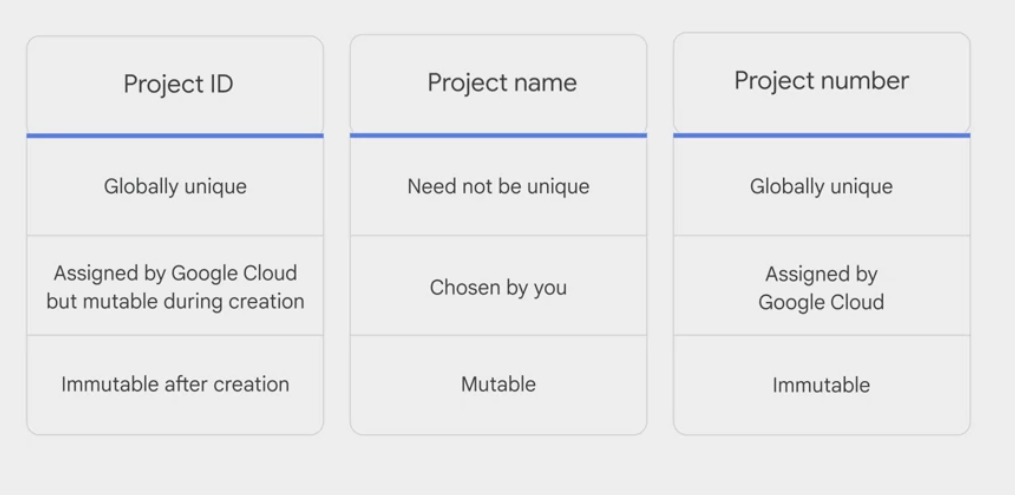
- labels are changeable, project ID and project number remain fixed.
IAM
IAM allows administrators to define who can do what and on which resources within an organization.
IAM policies consist of a “who” (principal) and a “can do what” (role).
IAM principle
- The “who”
- can be a Google account, a Google group, a service account, or a Cloud Identity domain.
- email address
IAM Roles
- The “What”
- IAM roles are collections of permissions that are granted to principals.
- Roles can be basic, predefined, or custom.
3 types of IAM roles
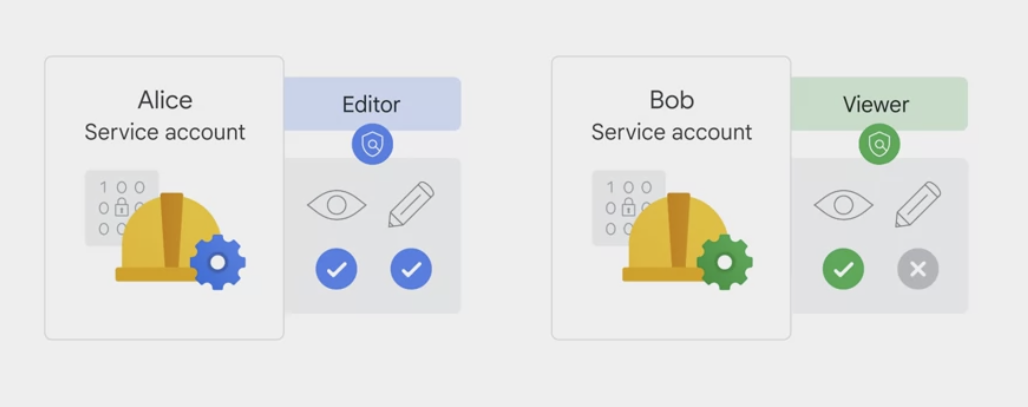
Basic role
- apply across all GCP services in a project
- affect all resources in a GCP project.
Basic roles include owner, editor, viewer, and billing administrator.

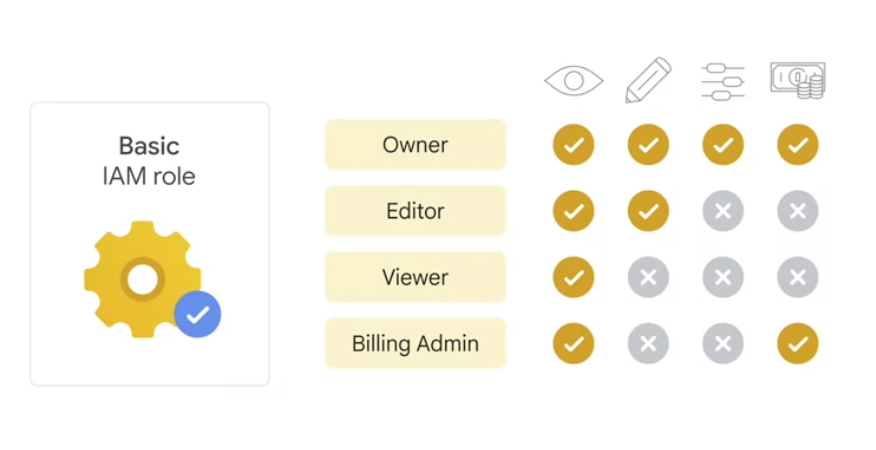
- May too sensitive to apply
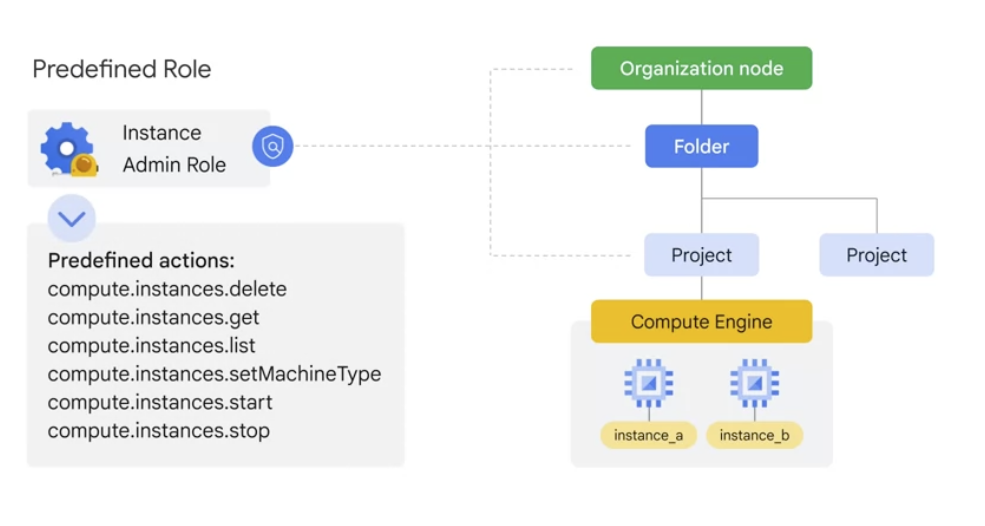
Predefined role
- apply access to particular GCP services in a project
- specific to Google Cloud services and define where they can be applied.
custom role
- define a precise set of permissions
- custom roles can only be applied to either the project level or organization level .
- can’t be applied to the folder level
.

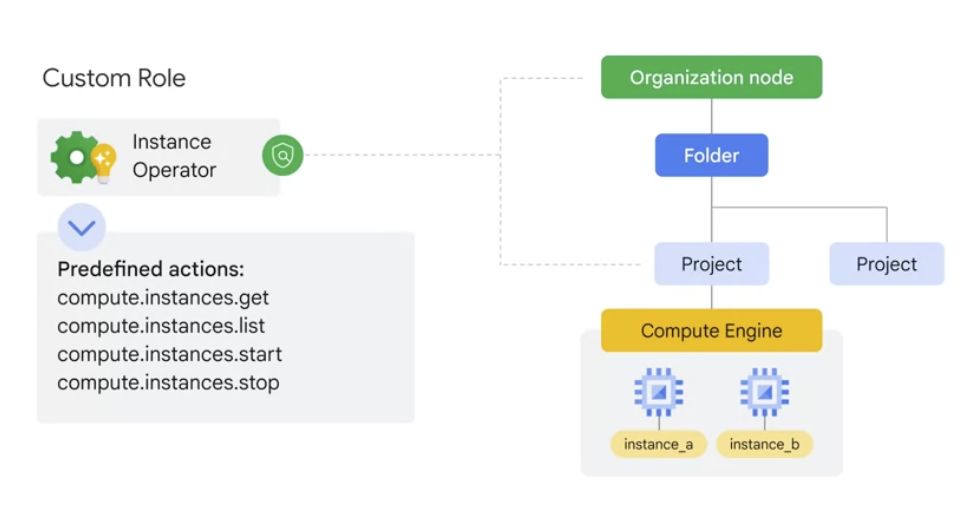
IAM policy
IAM policies can include deny rules to restrict certain principals from using certain permissions.
Deny policies are checked before allow policies.
member
- Google account,
- service account,
- Google Group,
- Cloud Identity or google wokrspace domain
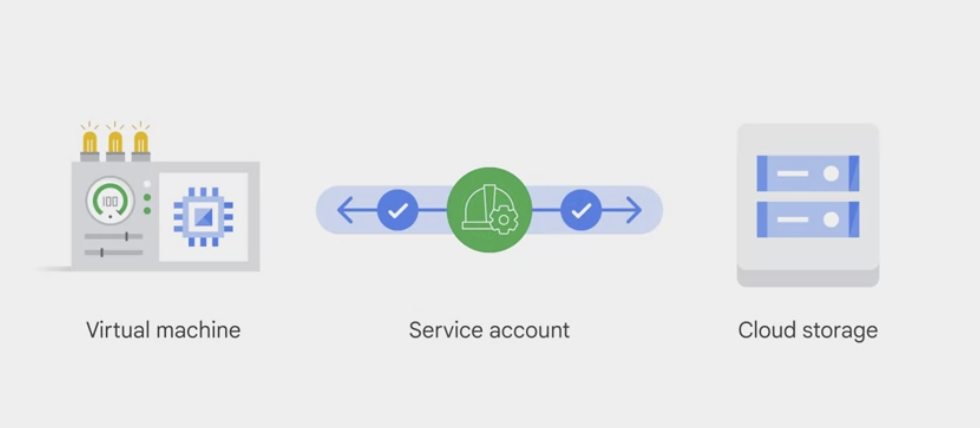
Service account
- a special type of Google account
- belongs to an application or a VM, instead of to an individual end user.
- to restrict the actions a resource (such as a VM) can perform
- to allow users to act with service account permissions
- Authentication between Google Cloud Platform services
scope
example
authenticate with keys
- rotation: 2 weeks
Access
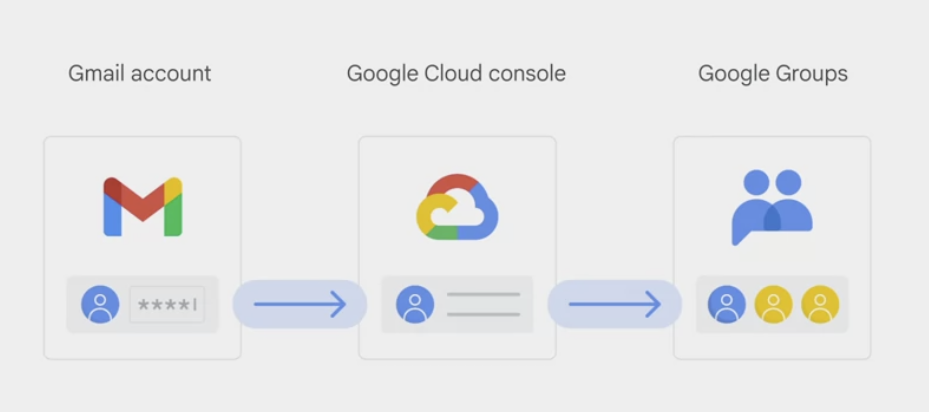
Cloud Identity
a solution for managing users and groups in Google Cloud.
Admins can log in and manage Google Cloud resources using the same usernames and passwords used in existing Active Directory or LDAP systems.
Cloud Identity offers a free edition and a premium edition with additional capabilities for managing mobile devices.
When someone leaves an organization, an administrator can use the Google Admin Console to disable their account and remove them from groups.
Google Workspace customers already have access to this functionality in the Google Admin Console.
sync Directory
SSO
best practise
.
































Comments powered by Disqus.