
Palo Alto Networks - Prisma Manage Prisma Cloud Alerts
[toc] Manage Prisma Cloud Alerts Core Concepts Prisma Cloud Core Concepts 4 main Prisma Cloud concepts: resource, policy, alert rule, and alert. resource a...

[toc] Manage Prisma Cloud Alerts Core Concepts Prisma Cloud Core Concepts 4 main Prisma Cloud concepts: resource, policy, alert rule, and alert. resource a...

[toc] Prisma Cloud - Generating Report – Generate and Download Compliance Reports Available Compliance Reports in Prisma Cloud Unlike the Asset Inventory Dashboard that aggregates all your...

[toc] Manage Administrators Prisma Cloud Administrator Roles Manage the individuals who can access instance by defining them as users in the system. Create account groups, and assign us...

[toc] Onboarding and Initial Setup Prisma Cloud Overview Prisma Cloud a cloud infrastructure security solution a Security Operations Center (SOC) enablement tool to address risks and ...

[toc] Cortex SOAR Security Orchestration an environment with applications targeted at current security operations team needs Positioning Cortex XSOAR Orchestration Orche...

[toc] AutoFocus: Prioritize, Research, and Mitigate Threats AutoFocus: Introduction .
System Design - Key Concepts Handling the Question Design Algorithms that Scale Key Concepts Horizontal vs. Vertical Scaling Load Balancer ...
[toc] Jackson反序列化漏洞分析 anatomy of a vulnerability class 0x00 前言 analyzed an application which used the Jackson library for deserializing JSONs. 反序列化JSON数据。 JSON is a format that encodes ...
[toc] Create SOCKS Tunnel to route Web Traffic Securely Without a VPN Prerequisites Step 1 (macOS/Linux) — Setting Up the Tunnel Step 1 (Windows) — Setting Up the Tunnel Step 2 — Configu...

pentest kali Tools snort network Network Protocol Port NAT .

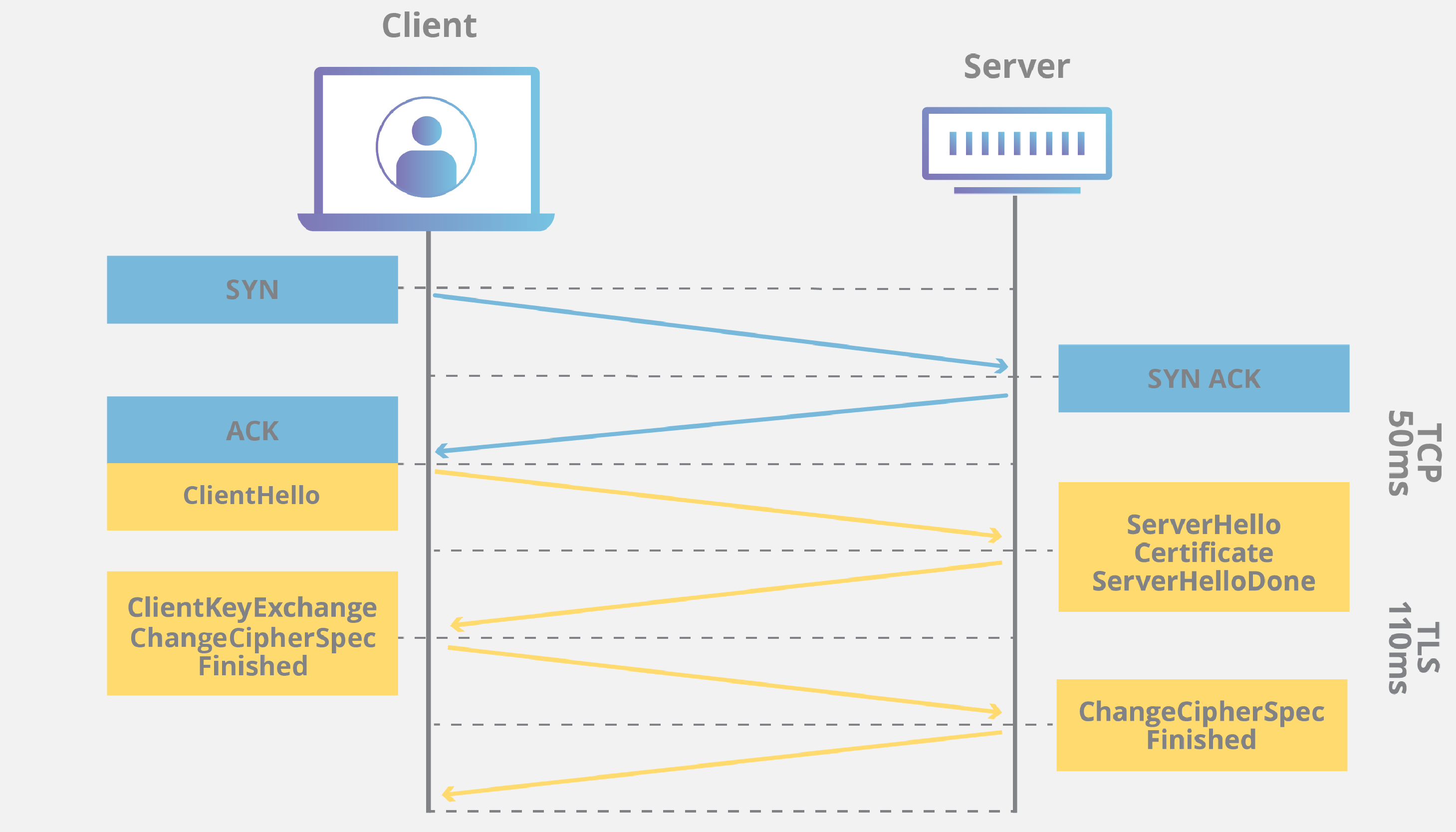
[toc] HSTS - HTTP Strict Transport Security The HTTP Strict Transport Security (HSTS) header a web security policy mechanism web sites communicate to browsers that all traffic exchanged ...
[toc] Shell grammar Simple Commands A simple command is an optional sequence of variable assignments followed by blank-separated words and redirections, and terminated by a control operator. ...
[toc] bash Note Number of elements: ${#ARRAY[@]} echo ${ARRAY[@]} stdin # standard input. It takes text as input. stdout # standard output. The text output of a command is stored in the stdo...
[toc] People :bowtie: :bowtie: :smile: :smile: :laughing: :laughing: :blush: :blush: :smiley: :smiley: :relaxed: :relaxed: ...
Markdown clolr change pic/gif size Markdown数学公式语法 0. 行内与独行 1. 向量公式 2. 分段函数 分段函数 方程组 ...